Cutting Edge Approach to Safeguarding your Business Assets
Cutting Edge Approach to Safeguarding your Business Assets
A Holistic Approach to Safeguarding your Business Assets

of Cybercrime Resolved
Security Assessments
Completed
GLOBAL TOP PLAYERS
QyReports
2018 SURVEY
Cases of Cybercrime Resolved
Security Assessments Completed
Compliance Audits Done
Penetration Tests Completed
We help organizations protect their brand, people, assets, and profits.
We help organizations protect their brand, people, assets, and profits.
4 VERTICALS OF
CYBERSECURITY

Training

Services
Our services are designed to cover all aspects of your organization’s security needs in today’s digital world.

Research

Development
4 VERTICALS OF
CYBERSECURITY

Training

Services
Our services are designed to cover all aspects of your organization’s security needs in today’s digital world.

Research

Development
4 VERTICALS OF
CYBERSECURITY

Training

Services
Our services are designed to cover all aspects of your organization’s security needs in today’s digital world.

Research
Staying up-to-date in an ever evolving world of cybersecurity, cyber threats, regulations, and more.
Development
Development of comprehensive security solutions that are ready-to-implement in today’s organizations.
Trusted by the best
Cycops has positioned itself as a premiere choice for top-level organizations looking for comprehensive security solutions, across the country and around the globe.




























Trusted by the best
Cycops has positioned itself as a premiere choice for top-level organizations looking for comprehensive security solutions, across the country and around the globe.





























Managed Security Services

Security Testing

Compliance Verification

Security Architecture & Design Implementation

SOC Management

Security Incident Response

Network Decontamination
Managed Security Services

Security Testing

Compliance Verification

Security Architecture & Design Implementation

SOC Management

Security Incident Response

Network Decontamination
Solving cybersecurity challenges in every industry, every day.
Solving cybersecurity challenges in every industry, every day.
Solving cybersecurity challenges in every industry, every day.
Solving cybersecurity challenges in every industry, every day.

Defense & Law Enforcement

NBFC & Microfinance

Information Technology

Pharma & Healthcare

Education Industry

ITES

Consulting & Recruiting

Shipping & Logistics

Hotels & Hospitality

Insurance

Manufacturing

Food Processing

Retail

BPO & KPO

Infrastructure
Cybersecurity in your Organization
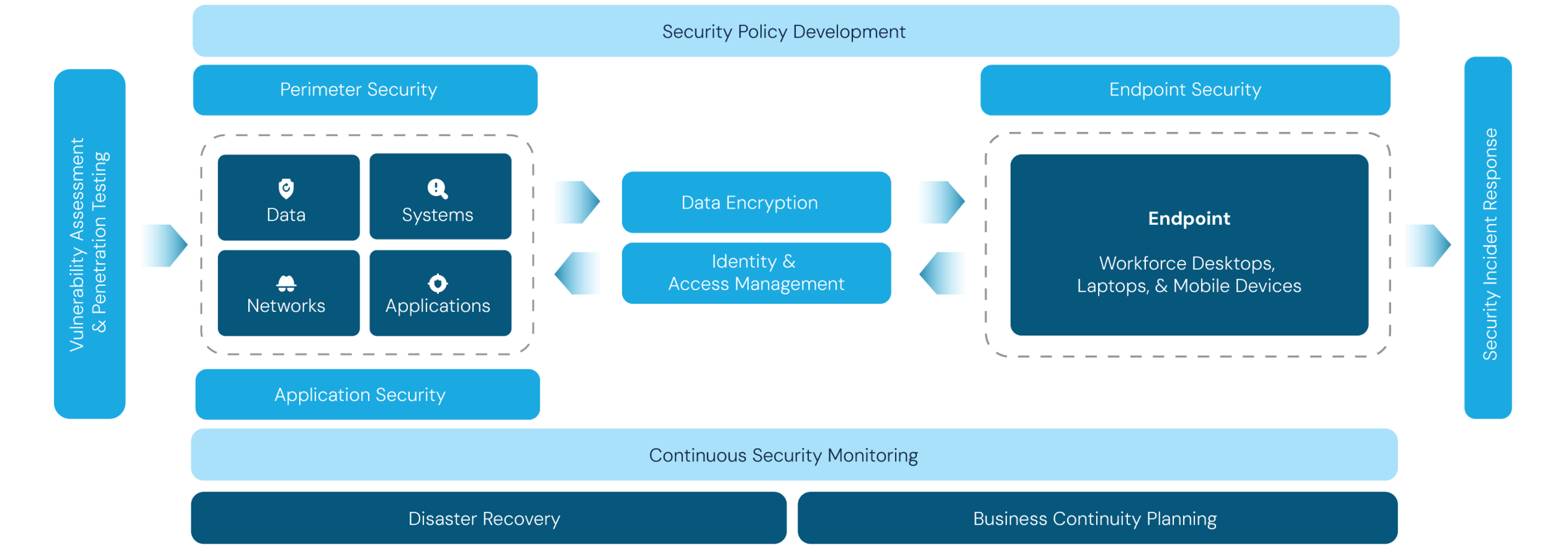
Role of Cybersecurity
Cybersecurity plays a crucial role in safeguarding an organization’s digital assets, sensitive data, and overall operations from a wide range of cyber threats. By implementing robust cybersecurity measures, organizations can mitigate risks associated with unauthorized access, data breaches, malware attacks, and other malicious activities.
Beyond protecting valuable information, cybersecurity also helps preserve brand reputation. Cybersecurity is an essential component of a resilient and well-functioning organization, providing the necessary foundation for sustainable growth and success in the digital age.
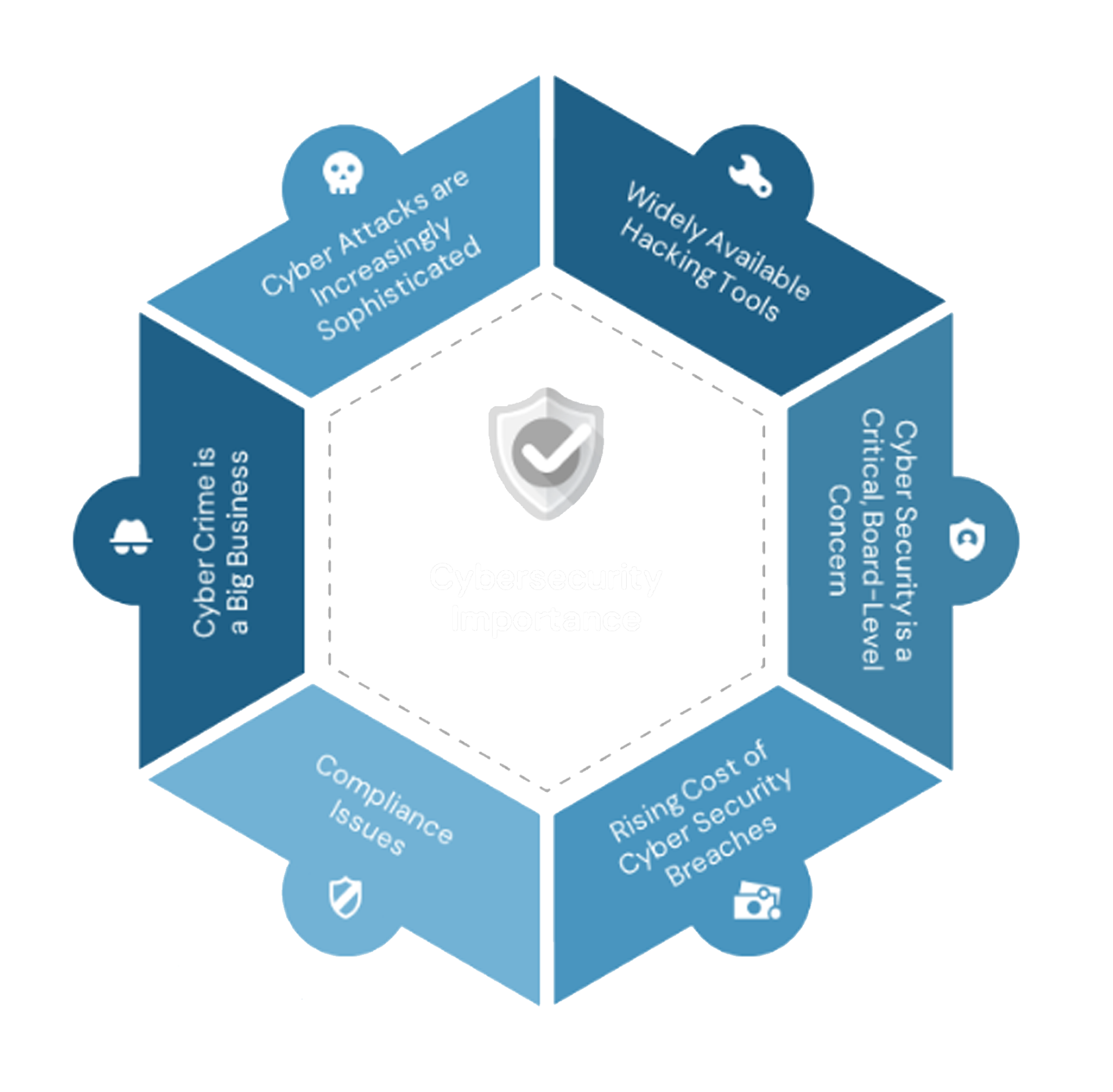
Cybersecurity in your Organization
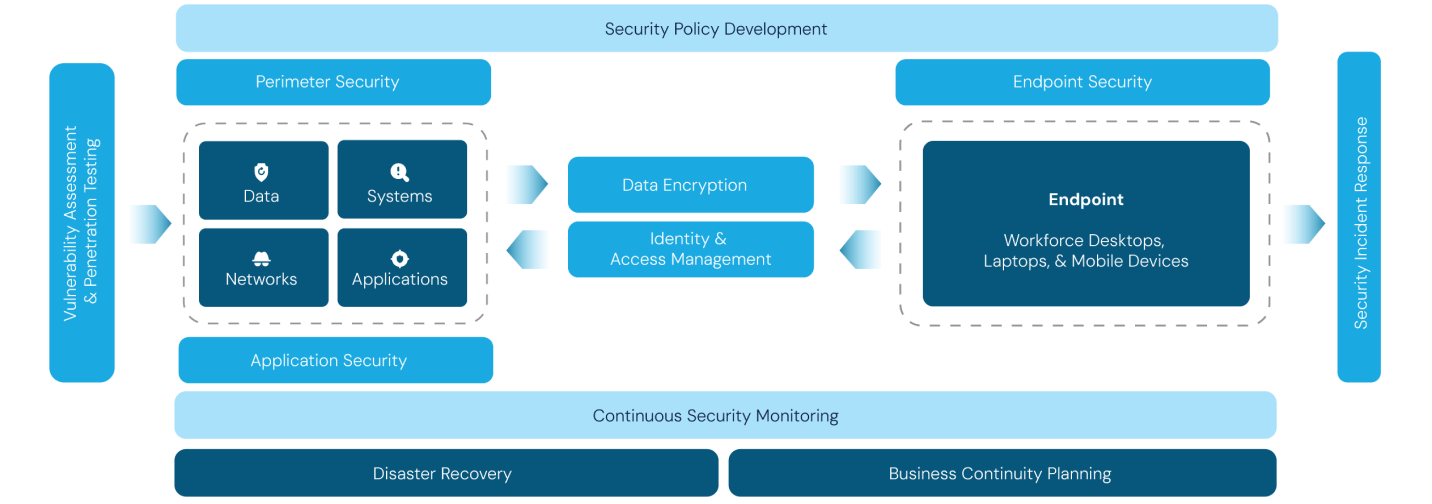
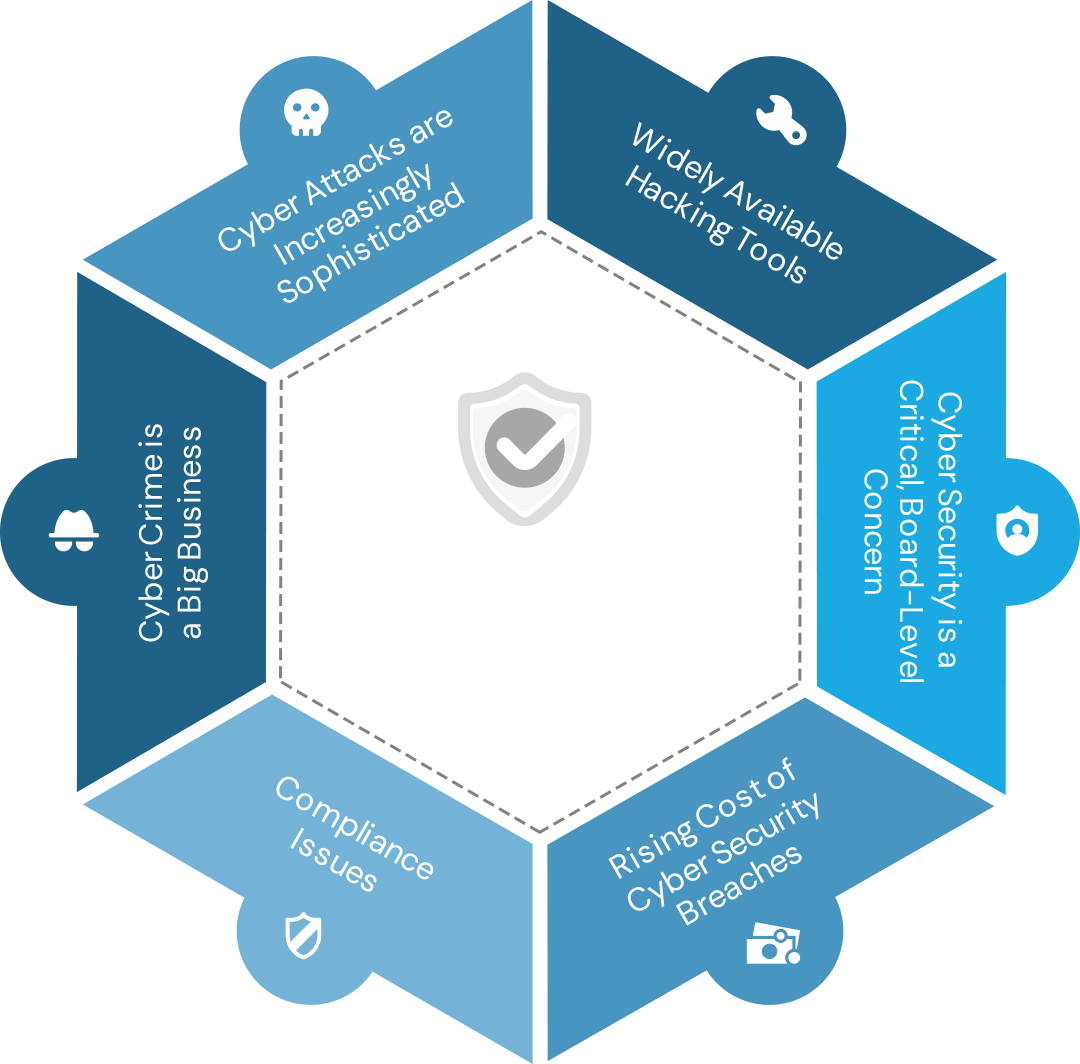
Cybersecurity plays a crucial role in safeguarding an organization’s digital assets, sensitive data, and overall operations from a wide range of cyber threats. By implementing robust cybersecurity measures, organizations can mitigate risks associated with unauthorized access, data breaches, malware attacks, and other malicious activities.
Beyond protecting valuable information, cybersecurity also helps preserve brand reputation. Cybersecurity is an essential component of a resilient and well-functioning organization, providing the necessary foundation for sustainable growth and success in the digital age.
Case Studies

Secure Software Development Implementation
about This organization was a well-established (Inc 5000) software development company that provided financial and Healthcare solutions. Initial VAPT Assessment The client employed 260+ IT

ISMS Audit and Implementation Service
about ABC Organization is a prominent Information Technology and Business Consulting firm offering project- based solutions, software solutions, and professional staffing services. With a customer-centric

Vulnerability Assessment and Penetration testing
about Client Acme (Pseudonymized) is a globally renowned international business school known for its excellence in education and research. With a diverse and large student
Enquire about cybersecurity for your organization.
We’re happy to answer any questions you may have and help you determine how our services best fit your needs.
Call our Global Offices:
India Office
United States Office
United Kingdom Office
Email Us : info@cycops.co.in
What happens next?
We Schedule a call at your convenience
We do a discovery and consulting meting
We prepare a proposal
Schedule a Free Consultation
Recognized by the best
The company needed to complete a complex migration on a tight deadline to avoid millions of dollars in post-contract fees and fines.




















